Jim2 Multi-Factor Authentication – Keep your crucial Jim2 data safe
A Jim2 On-premises customer experienced every business’ worst nightmare when their system was attacked and rendered inaccessible by hackers.
Isaac Edmiston, Director of Sales and Marketing at Norweld Australia explained in their case study:
“In July 2017, our server was hacked in a ransomware attack. All programs hosted on the server were immediately not accessible – including Jim2. All staff, from the workshop employees to the managing director, experienced a substantial amount of lost time as a result of no system access.”
Luckily, due to diligent backups and Happen Business being able to quickly move their system and data into Jim2Cloud. Soon they were back to business, as normal.
Read the full Norweld case study here.
Since Jim2 Version 4.5 was released in mid-2024, this added security layer is now available to be enabled to protect your crucial business data.
Research conducted by Microsoft found that MFA leads to a 99.22% reduction in the risk of compromise across the entire population, and a 98.56% reduction even in cases where credentials were leaked.
What is MFA?
Multi-factor Authentication (MFA) is used to enhance security by requiring users to provide multiple forms of digital identification to access an account or system. This extra layer of security makes it significantly harder for unauthorised individuals to gain access, even if they manage to obtain one factor like a password. MFA protects against various threats, including phishing attacks, password reuse, and brute-force attacks.
The benefits of implementing MFA:
Increased Security: MFA adds an extra layer of protection beyond just a password, making it much more difficult for hackers to compromise accounts.
Mitigates Password-Related Risks: Many cyberattacks rely on stolen or compromised passwords. MFA helps neutralise these risks by requiring additional verification methods.
Protects Against Phishing: MFA can protect against phishing attacks, where users are tricked into revealing their credentials, as attackers would still need the second authentication factor.
Reduces the Impact of Password Reuse: Even if a password is compromised on one site, MFA can prevent it from being used to access other accounts because the second factor is usually unique to each service.
Defends Against Brute-Force Attacks: MFA makes it harder for attackers to guess passwords through brute-force methods, as they would also need to bypass the second authentication factor.
Enabling Jim2 MFA Tools
About Jim2Cloud Multi-Factor Authentication – Ensuring double strength security
Jim2Cloud offers two levels of MFA – one that protects Jim2Cloud and a second optional layer that protects the actual Jim2 client application.
Jim2Cloud MFA protects access to Jim2Cloud on login, prior to launching Jim2.
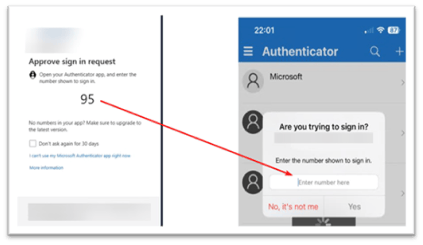
About Jim2 Client Multi-Factor Authentication
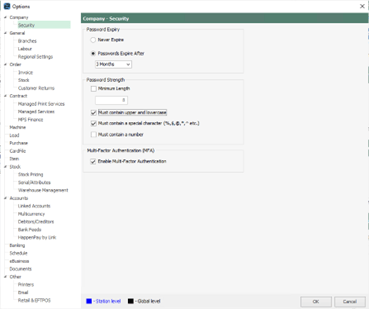
For Jim2 clients with their own on-premises hardware, MFA can be enabled by ticking on the Tools > Company > Security > Multi-Factor Authentication > Tick Box
Jim2 MFA occurs during login to the database via the Jim2 Client. Both Jim2Cloud and Jim2 On-premises customers can optionally configure Jim2 MFA on their database.
Follow the Setup instructions here in Jim2 Help.

Gain Herd Immunity with Multi-factor Authentication
While it’s an extra step to verify that your login access is authentic, it is worth considering other benefits of embracing MFA:
Cost-Effectiveness: While there’s a cost associated with implementing MFA, it’s often far less than the cost of a data breach or the fines associated with non-compliance.
Future-Proof Security: MFA solutions can adapt to evolving cyber threats and offer flexibility in authentication methods, making them a sustainable security solution.
Scalability and Accessibility: Cloud-based MFA solutions can be easily scaled to accommodate growing user bases and are accessible from various devices.
Protection Against Insider Threats: MFA helps to mitigate the risks associated with compromised or malicious insider access.
Examples of MFA: Common examples include using a password along with a one-time code sent to a mobile phone app, fingerprint or facial recognition, or a unique security key.
Next Steps
Watch Ashley guide us through the steps to set up Multi-Factor Authentication in Jim2 Version 4.5.
We recommend adjusting the video quality setting on YouTube to 1080p for the best viewing experience.
Useful Resources
- Jim2 Multi-Factor Authentication – Visit Jim2 Help
- Introduction to Jim2 Multi-Factor Authentication in Version 4.5 – Visit the Learning Centre
- Jim2 Guide to Backups – Visit the Learning Centre
Need assistance from the Jim2 Support Team?
Reach out to our support team with your questions on MFA in Jim2.


































